Hi Guys this is Rajesh from elearninginfoit.com today We are going to talk about the Trend micro and the product name would be Trend micro deep security version 20. Now let’s start with Trend micro deep security but before that one small piece of information about this post.

Table of Contents
Objective
- We’ll describe the purpose feature, function, and capabilities of Trend Micro Deep Security,
- Define and install components that make up deep security
- Implementation of security by enabling it. Protection models.
- review, all available configurations, and administration option
Overview Trend Micro Deep Security 2022
We are going to understand how deep security exactly works. And what components are there, that we can utilize now, but who can read this post? IT professional is responsible for protecting network data center and cloud resources from data bridges and targeted attacks.
This includes those involved with operations, deployment, security, response, and compliance. So if you are involved in any of the operational or administrative level tasks, then you must watch the studio. And guys, if you have basic knowledge of the following, It’s also beneficial like windows servers and client firewalls and packets inspection devices, VMware ESXi, we center NS.
Prerequisites for Deep Security Manager
These are the applications of the works where we usually deploy the server as well as Amazon, AWS, Microsoft, Azure, VMware, we cloud those are the cloud waste services and, uh, virtualization technology.
So I hope you all have knowledge of these particular technologies. And print after competing in this entire series, you will be definitely able to identify the key business drivers for the Deep security list.
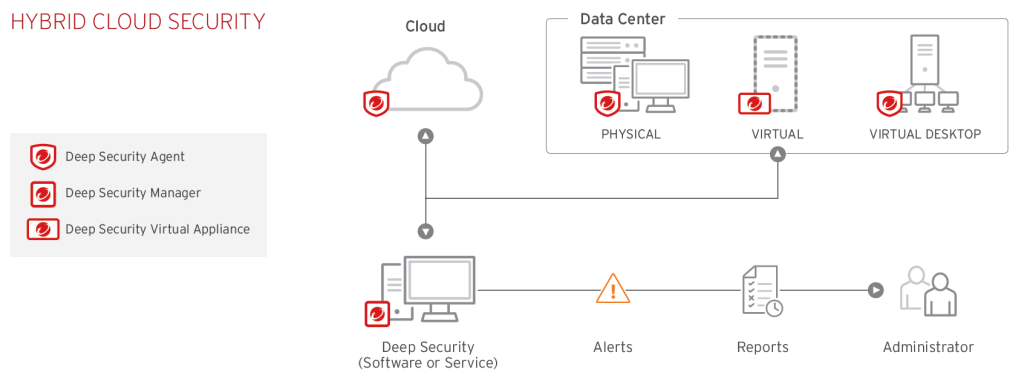
Deep security protection models
The Deep Security deployment option, identifies the roles of each of the Deep security protection models list that require and option components of Deep security installation. Now print, before us, uh, start the discussion of Deep security,
let’s review that security solution offered. Trend Micro provides layer content security with an interconnecting solution that shares data so that you can protect your user’s network data center, and cloud resources from data bridges and targeted attacks.
So there are multiple products that come into this particular four segment. Right now. We are not going to do the deep dive, but we’ll cover all those products in different, different series. But if you want here, just one small recap, like user protection, an interconnected suite of security products and advanced.

Depends on techniques that protect users from ransomware and other threats. Another is network depends. It’s a next-generation IPS.
. And bridge detection to prevent targeted attacks, advanced threats, and ransomware from embedding or spreading within the network hybrid cloud comprehensive automated security solution to protect enterprise workload in the data center and the cloud from critical new.
While helping to accelerate regulatory compliance, and visibility control, manage a comprehensive set up security capabilities from one single management consult. So if you have multiple Trend micro applications, then also you can manage from the single console.
Now smart protection network. It’s provided up to the second threat intelligence to immediately stamp out the attack before they can harm valuable data.
Since we’re talking about deep security, so let’s understand the evolution of the data center workloads in the data center started opening physical servers. As you know, was probably the very first when companies or data centers were built. So those are using physical servers. And at that time, the people who manage this server, they have to maintain thousand thousands of servers.

In a data center and which was a very critical task. But later on, everything is moved to virtual, which means in a single server, we can create multiple virtual operating systems for our application.
Then again, it moved to the cloud, and now containers and servers. So I hope you all know what the, uh, physical virtual cloud air containers and serverless, now print let’s understand.
Hybrid cloud solution C. Nowadays it’s dynamic because they’re evolving infrastructure from the physical virtual cloud and then serverless.
So you can see the, how exactly is growing as well as the speed up app changes, which means nowadays if you observe in your mobile, so we are continuously getting updates or the, you know, and the way application works is getting completed.
And then the last one is threat sophistication because we don’t know whether we really got impacted or we have, uh, malware presenting our machine or not now the organization pin threat protection and audit because if you have multiple environments like your physical server, virtual server, cloud, or server list, then at the time you have, you probably need to deploy multiple intervals from multiple.
Okay, so here, deep security comes into the picture. Deep Security is supported for all these various environments. A deep security agent can provide, you know, protection to all the applications, as well as the server infrastructure. And third is the lack of resources needed to simplify. So here is our answer is the same.
We have one agent which, you know, serves the purpose of all. Pain points. X means your pain point and Trend micro solves all your problems with one single solution and prince. These are the, you know, major pain point. All well, incompatible Audi two-minute tools, zero-day scan stone. But with Trend micro, you don’t have to worry about anything.

And these things we are going to learn in our next post. Now guys, just let me tell you deep security platform. The core of the Trend micro hybrid cloud security solution. Okay. Because deep security provides advanced server security for physical virtual cloud-based computers.
It also protects enterprise applications and data from bridges and business disruption without requiring emergency patching.
And this is a centrally managed platform, that consolidates security operations within a single management dashboard for all capable.
And simplified security operations while enabling regulatory compliance and accelerating the ROI of virtualization and cloud projects.
And this is deep security. FIPS certified. And just for your information, deep security protects servers again, zero-day malware and ransomware identify suspicious Behavior and shield the network from vulnerability
Before they can exploit and detect and stop network-based attacks while minimizing the operational impact from resource inefficiencies and emergency patching. So we’ll cover this practically, but just, this is just for your information.
Key business drivers for deep security
Deep security products against data breaches and business, disruption, and friends.
Provision for full security capabilities automatically in the data centers, optimized data center, resources, support compliance, and the last one is reduced operational cost conference.
Deployment methods
Let’s understand what are the deployment methods or flexibility in deployment provided by Trend Micro.
So if you are on-primes server, you can install this software. This means if you have any windows server in your environment, then you can simply install the deep security manager in your environment and then deploy the agent on the rest of the machines.
And let’s say, if you don’t have any windows server, then at that time you can use the software as a service, which is a cloud place solution from, trend micro.
This also works the same, as on-premise, but the only practice in this very first scenario, you have to manage your servers. In the second scenario, we don’t have to manage infrastructure. I mean, your server, we just have to download the agent and deploy it on your node.
That’s it. And very important. The third one, the cloud marketplace, let’s say in the Amazon web services and Microsoft Azure marketplace, deep secret securities available as a software piece and as a service, which go ahead scan, purchase, and print.
Models of Deep Security
These are the actual models. Of deep security okay. On which we are going to work. It is anti-malware. The second is web reputation.
The third is application control for this log inspection PIP, this integrity monitoring, and six is a firewall. So as here is a basic idea of what exactly this model is going to work like.
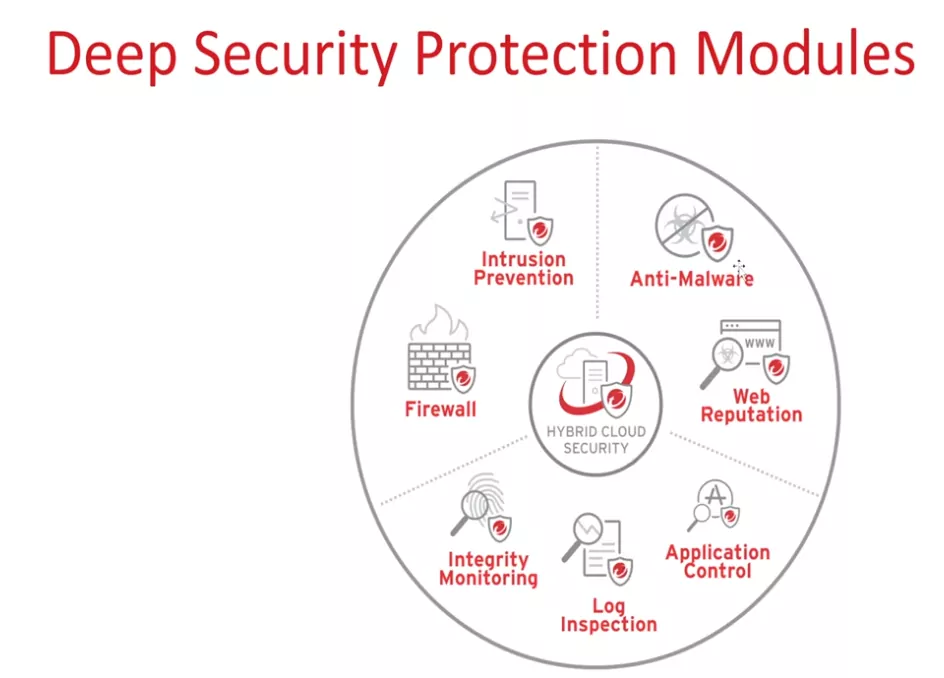
Anti-malware guys, the anti-malware model detect and blocks MES software, such as viruses, and other application intended to harm your endpoint. And this anti-malware protection can be offered in real-time, on-demand as well as on the shuttle. So the way you want to use this and you have the know complication options available in the console.
Web reputation whenever you browse any website on your machine. Okay. It tracks the credibility of the website to save our server from malicious URLs, which means while browsing, uh, Trend micro web reputation pound you’re visiting any ME’s website, then it has the capability to block that website immediately.
Next Firewall you can block malicious. Or let's say, allow block network traffic through a bidirectional stateful firewall, which means you can view all the traffics, which is coming to your server and going out from your server, and the basis on your requirement, you can block or allow those traffics. We can completely harden our server. I'll demonstrate this during the policy contribution.
Next is Intrusion Prevention. Intrusion prevention basically examines the alt incoming and outgoing traffic at the packet. Searching for protocol ions, policy violations, or any content that signals an attack and it detects and blocks known and unknown, as well as zero-day attacks that target venerability and print here, is a for virtual patching.
Virtual patching basically drops traffic, attempting to leverage unpatched venerability in the application or the operating system. This keeps the server. An endpoint is protected until relevant patches can be applied. Prince, let me explain this with, uh, one of the examples, let's say you have one of the windows servers and it's identified as a venerability able and Microsoft is just now released the patches to protect that venerability abilityBut as per its industry, we cannot directly deploy that. Patch on the server until we complete the. So in this situation, you can protect your, those servers using the
Trend micro intrusion prevention model, because without ensuring the actual patches or software on your windows server Trend micro can patch your, that particular one Liberty.Virtually. So this is one of the deal breaker components provided by Trend Micro.
This is a very much useful protocol, hygiene, protocol, hygiene, basically block traffic based on how it confirms protocol specifications, and allow DSS to detect packet fragment packet without plaques and similar anomalies. Friends.
Next integrity, monitoring integrity monitoring model monitors, critical operating system and application files, including directories, custom piles, logistics and values, open ports, processes, and services to provide real-time detection. Reporting of malicious and unexpected changes. And this model will track both authorized and unauthorized changes made on a server instance. It has the ability to detect unauthorized changes. With this model, you can get all the information. Which is done on that particular server, whether somebody changes any of the file permission or whatever is so whatever the, uh, rules you are going to configure in this, okay, you will get information.Whenever that particular action is performed based on your rule. So it'll detect and inform you.
Next log inspection with the log inspection model, collect and Analyze the operating system and application locks for suspicious Behavior, security events, and administrative events across the data center trends. This model. Optimize this, the identification of important security events borrowed in multiple log entries and suspicious injuries, or events can be forwarded. Yes, I am for correlation purposes.
Next Application Control this model completely logged down your entire operating system. So then, whatever the software is. Or you may say only approve applications can execute or stop specific unwanted software prompt from running. How exactly do workload we tell you when you deploy application control or let's say when you enable application control on any of the servers, it basically scans your entire server and whitelist list all the applications which are installed at the time of enabling. Application control. And once the application control is enabled in preventing more, then from that time onwards, Trend micro blocks, and all the new applications, get executed on that particular server. So this is a very interesting picture. Okay. So we'll test this also. Now guys, let's understand that Trend micro predictor.
Trend Micro Deep Security Architecture
This is one of the Architecture. And this is my server. As you can see right now, here, it’s through servers are configured. This is in the cluster, but in your environment, you can put it on the server or make it in a cluster in the cluster.
Also, the Trend micro servers work as active, active, not active, and passive it divides the load between these two servers.
if you have any questions contact us
Hope you like it:










